IPsec VPN Overview
(1) IPsec VPN Background
- IP protocol was designed in the early stages of the Internet where security wasn’t an issue
- IP protocol is vulnerable to many network attacks and introduce security issues
- IETF introduced IPsec as security extensions for IP protocol
- August 1995, IPsec was officially standardised by IETF in RFC 1825
What is VPN (Virtual Private Network)?
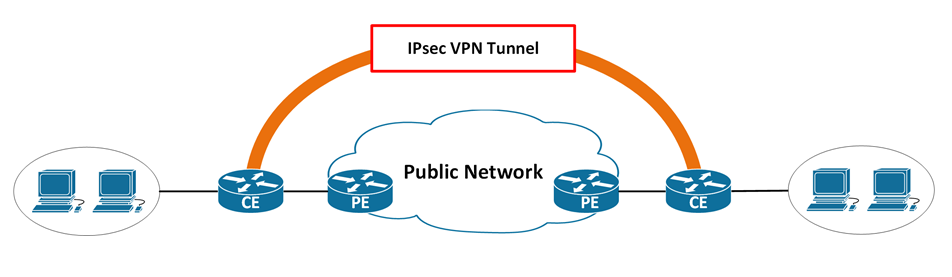
- A technique to securely and privately transmit data over a shared network infrastructure.
- Achieved by encapsulating, encrypting, authenticating the data traffic.
Type of VPN
- Site-to-Site VPN
- Allow network Site-A to has private connection to network Site-B via shared network infrastructure
- Remote Access VPN
- Allow remote client to has private connection to local office via shared network infrastructure
What is IPsec (IP Security)?
- A suite of protocols and algorithms to secure IP traffic communications.
- Achieved by defining what traffic to protect, how that traffic be protected, to whom the traffic is sent.
Why use IPsec VPN?
- Independent of Service Provider (SP) transport
- Customer-side provisioning, not SP-side provisioning
- Only require IPv4/IPv6 reachability as underlay transport
- Allows both site-to-site and remote access VPN
- Offers IPv4/IPv6 packet protection
(2) Key features of IPsec VPN:
- Data origin authentication
- Crypto peer authentication (PSK, RSA certificate) to ensure peer identity
- Data integrity authentication
- Data authentication (HMAC functions: MD5, SHA) to prevent MitM/session hijacking attack
- Data content confidentiality
- Data encryption (DES, 3DES, AES) to prevent eavesdropping attack
- Anti-replay protection
- Encrypted sequence numbers in data packets to prevent replay attack
- Non-repudiation
- Ensures that the sender cannot deny sending the data
IPsec typical business applications
Secure Branch-office to Head-office connectivity over the WAN/Internet
Secure remote access connection over the Internet
Secure WAN connection with 3rd party partners
IPsec VPN modes of operation:
Tunnel mode
- Introduce additional outer IP header (new IP address)
- Can be used as private IP address tunneling
- More secure because original IP header is hidden
- Typically used in gateway-to-gateway or host-to-gateway VPN scenarios
Transport mode
- Retain the original IP header
- Less overhead because no additional IP header
- Data plane must be sourced locally from Crypto endpoint itself
- Typically used in host-to-host VPN scenarios
- DMVPN application
Hi-level IPsec VPN process:
- Interesting traffic trigger the IPsec process
- Phase-1 tunnel setup
- Dynamic negotiation and secure key exchange using ISAKMP/IKE
- Used to secure Phase-2 tunnel setup
- Called IKE SA tunnel
- Phase-2 tunnel setup
- Dynamic negotiation and secure key exchange using ISAKMP/IKE
- Used to secure IPsec VPN packets (data plane)
- Called IPsec SA tunnel
- IPsec VPN packet forwarding and SA tunnel maintenance
(3) Cisco’s IPsec VPN deployment options
- Crypto map based: Legacy framework of IPsec VPN deployment and configuration
- Static crypto map: Statically configured remote peer and crypto-protected address space
- Dynamic crypto map: Dynamically allocates remote peers to pre-defined array based on their provided information
- GRE based: GRE IP over IPsec, IPsec VPN with GRE tunnel interface
- VTI: Simplifies IPsec VPN configuration and encapsulation with IPsec tunnel interface
- SVTI: Statically configured IPsec tunnel interface
- DVTI: Dynamically created IPsec Virtual-Access tunnel interface from pre-defined Virtual Template (Enhanced EzVPN)
- DMVPN based: mGRE over IPsec, IPsec VPN with DMVPN tunnel interface
- GETVPN: Large scale any-to-any tunnel-less IPsec VPN
- EzVPN: Framework of Cisco IPsec VPN deployment and configuration with IKEv1
- FlexVPN: Framework of Cisco IPsec VPN deployment and configuration with IKEv2

0 Comments