IPsec VPN Stateless High Availability
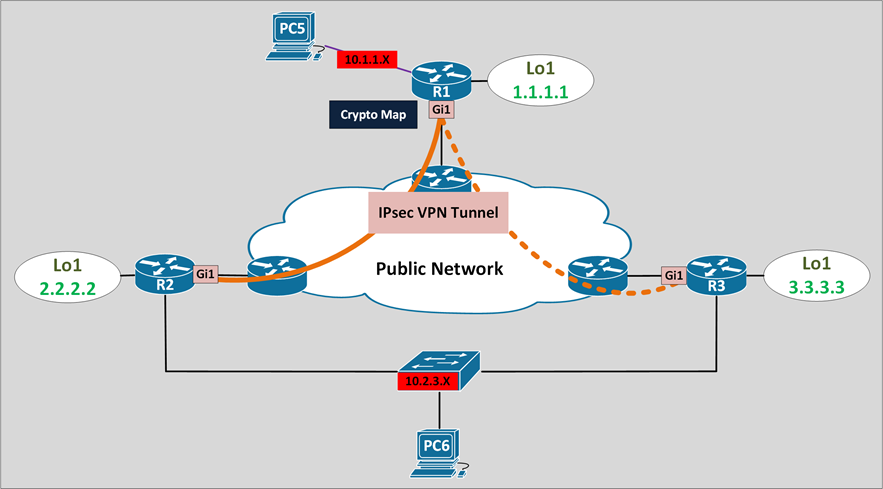
IPsec VPN “stateless” failover
- IPsec VPN uses R1 and R2 tunnel as a primary path
- IPsec VPN uses R1 and R2 tunnel as a backup path
- Only 1 IPsec peer is active at a time, in this case it’s the primary path
- If primary path failed, R1 need to negotiate new SAs with R3 (IKE SA and IPsec SA)
- Stateless means there is no backup copy of primary/existing SAs on the backup path/device
IPsec VPN Crypto Map Based failover scenario
R1 is configured with a redundant peer and pre-shared key, only 1 peer will be UP at a time
- R1(config)#crypto isakmp key CRYPTO_KEY address 2.2.2.2
- R1(config)#crypto isakmp key CRYPTO_KEY address 3.3.3.3
- R1(config)#crypto map MAP1 10 ipsec-isakmp
- R1(config-crypto-map)#set peer 2.2.2.2
- R1(config-crypto-map)#set peer 3.3.3.3
R1 use DPD to detect failure peer and failover between primary peer and backup peer
- R1(config)#crypto isakmp keepalive 10
- R2(config)#crypto isakmp keepalive 10
- R3(config)#crypto isakmp keepalive 10
R2 and R3 need to do RRI to signal the routing protocol which router is the active peer
- Consider the “Switch” act as a gateway for PC6, and act as an IGP peer for R2 and R3
- R2(config-crypto-map)#reverse-route remote-peer 1.1.1.1 gateway
- R3(config-crypto-map)#reverse-route remote-peer 1.1.1.1 gateway
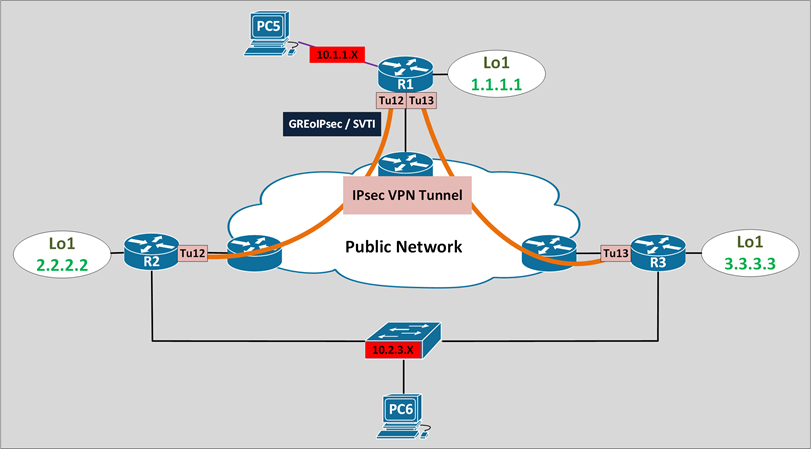
IPsec VPN with GRE failover scenario
R1 is configured with 2 GREoIPsec Tunnels, failover options:
- Through DPD
- Delete IKE SA and IPsec SA if failure detected
- Through tunnel keepalive
- Only for GRE point-to-point
- Bring down tunnel interface if failure detected
- Through routing protocol adjacency
- Bring down neighbor and delete route if failure detected
IPsec VPN with SVTI failover scenario
R1 is configured with 2 VTI Tunnels, failover options:
- Through DPD
- Delete IKE SA and IPsec SA if failure detected
- Through routing protocol adjacency
- Bring down neighbor and delete route if failure detected

0 Comments