IPsec VPN With DMVPN Overview
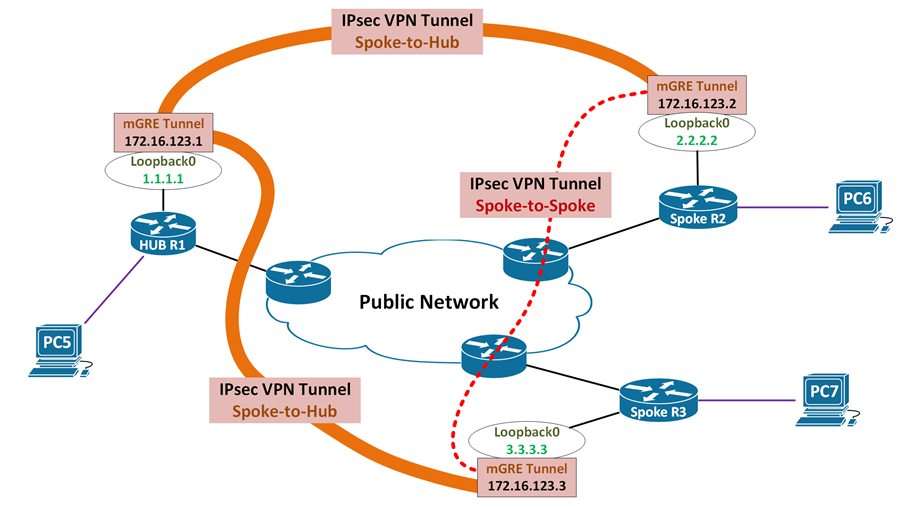
IPsec VPN with DMVPN overview
- IPsec integrated with DMVPN, but not a must
- Configured as crypto ipsec profile on Tunnel interface (mGRE)
- Dynamic spoke-to-spoke tunnels is supported
- The order of operation
- Underlay routing
- Packets encapsulated in GRE, then encrypted with IPsec
- NHRP controls the the tunnels
- Overlay routing
- Bringing up a tunnel
- NHRP signals IPsec to setup encryption
- IKE/ISAKMP phase 1 & phase 2 negotiation
- IPsec responds to NHRP and the tunnel is activated
- All NHRP and data traffic is encrypted
- Bringing down a tunnel
- NHRP signals IPsec to tear down tunnel
- If encryption is cleared or lost, IPsec can signal NHRP to clear the tunnel
- Spoke to hub tunnels are always nailed up (All DMVPN phases)
- Hub always has IPsec SA for all spokes
- Spoke to spoke tunnels are on demand (DMVPN phase 2 and 3)
Redundancy consideration
- IPsec stateful failover isn’t supported
- Invalid SPI recovery is not useful with DMVPN
- #no crypto isakmp invalid-spi-recovery
- Sharing the IPsec SADB between tunnels
- When using same IPsec profile and tunnel source (must use the interface name)
- If IPsec SA sessions aren’t shared within same SADB, the SA may get associated with wrong SADB with wrong interface. (Duplicates SAs and tunnel flapping)
- #tunnel protection ipsec profile VPNPROF1 shared
- Crypto peers monitoring
- ISAKMP keepalives on spokes (DPD) for underlay ISAKMP monitoring
- BFD over DMVPN for fast overlay tunnel monitoring (IOS XE 16.3.1 or later)
Crypto best practice
- BFD over DMVPN for quick spoke-hub and spoke-spoke tunnel recovery
- IKE/ISAKMP keepalives on spokes only
- #crypto isakmp keepalive 30 5 [on-demand | periodic]
- #crypto isakmp nat keepalive 30
- CPU/Memory on hubs only
- #crypto call admission limit ike <sa | in-negotiation> <max-SAs>
- #crypto ikev2 limit max-in-negotiation-sa <max-SAs> <inbound | outbound>
- #show crypto call admission statistics
Scaling IPsec over DMVPN
- As DMVPN cloud grows, IPsec state grows
- Linier IPsec SA state from hub to spokes, spoke-to-spoke scale is on-demand
- Scaling ISAKMP authentication
- PSK is supported but hard to manage
- Wildcard PSKs are a bad idea
- PKI is the preferred solution
- Scaling IPsec SAs
- DMVPN over GETVPN

0 Comments