ISAKMP IKE Phase 1 Details
(1) ISAKMP and IKE Overview
ISAKMP and IKE background
- Manual keying presents many challenges and disadvantages
- November 1998, IETF specified a framework to address these issues
- ISAKMP was officially standardised by IETF in RFC 2407, 2408
- IKE was officially standardised by IETF in RFC 2409
- The vast majority of IPsec leverage the scalability features provided by ISAKMP and IKE
- IKE/ISAKMP key functions
- Dynamically and securely exchange keys
- Negotiate security parameters
ISAKMP and IKE Overview
ISAKMP “Internet Security Association and Key Management Protocol”
- Protocol framework for establishing security context, defines the procedures for:
- Payload formats of communication
- The mechanics of implementing a key exchange protocol
- The negotiation of a security association
- Protocol used for key exchange and SA negotiation: IKE, Oakley, SKEME
- IKE protocol is being used for IPsec VPN
- IKE is hybrid protocol, combines the strengths of Oakley and SKEME protocols
IKE “Internet Key Exchange”
- Protocol that is used by IPsec for establishing security context, and defines the actual mechanics for the process:
- Authentication of the IPSec peers
- Negotiates IPSec keys
- Negotiates IPSec security associations
* ISAKMP/IKE occurs in 2 phases: Phase-1 and Phase-2.
(2) ISAKMP/IKE Phase 1:
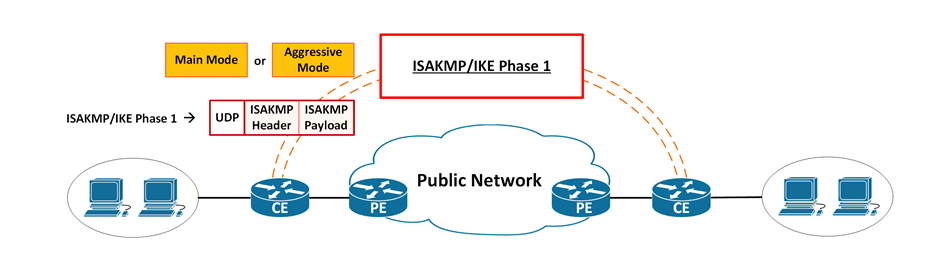
Phase 1
- Authenticates and protects the identities of the IPSec peers (identities protection only available in Main mode)
- Negotiates a matching IKE SA policy between peers to protect the IKE exchange
- Performs an authenticated Diffie-Hellman exchange with the end result of having matching shared secret keys
- Establishes IKE SA
- Sets up a bidirectional (2-ways) secure tunnel to negotiate IKE phase 2 parameters
*Phase-1 has 2 modes: Main mode, Aggressive mode.
Main Mode
- Main mode has three “two-way exchanges” (6 messages in total)
- Offers identity protection (through encryption)
- 1st exchange (negotiate policy)
- Encryption algorithm (DES / 3DES / AES)
- HMAC function (MD5 / SHA)
- Crypto peer authentication type (PSK / RSA Certificate)
- Diffie-Hellman key group
- SA lifetime
- 2nd exchange (exchange DH public values and ancillary data)
- Public keys, Nonces are sent for a Diffie-Hellman exchange
- Nonces: random numbers each party must sign and return to prove their identities
- 3rd exchange (authenticate the DH Exchange)
- Encrypted identity exchange
- Identity verification confirmation (hash payload)
Aggressive Mode
- Aggresive mode has two exchanges (3 messages in total)
- Offers speed and lightweight (no identity protection)
- It’s possible to “sniff” the wire and discover who formed the new SA. However, it is faster than main mode.
- 1st exchange
- Encryption algorithm, HMAC function, Device authentication type
- Diffie-Hellman key group, SA lifetime
- Public key, nonces are sent for a Diffie-Hellman exchange
- Identity exchange
- 2nd exchange
- Identity verification confirmation (hash payload)

0 Comments