IPsec VPN Crypto Map Based Overview
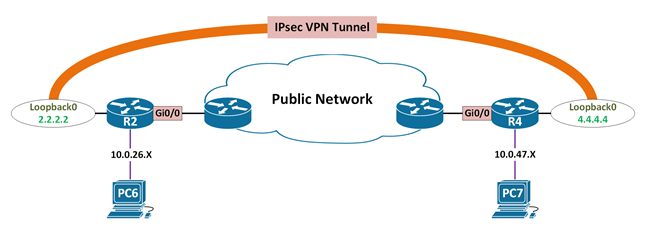
Crypto Map Based IPsec Overview
- “Legacy” method of IOS IPsec configuration
- Still the most common method
- Used to form on-demand IPsec tunnels
- Session initiated only when interesting traffic detected
- No dynamic routing support through tunnel
- Not without addional encapsulation such as GRE
How Crypto Map works
- Crypto map is a data-plane filter
- Matching traffic triggers an ISAKMP session to start
- Traffic is matched using ACLs
- ACLs define Proxy IDs for IPsec Phase 2
- Allows for granular control over VPN traffic using extended ACL
Applying Crypto Map
- Crypto map apply to L3 outgoing interface
- Only one crypto map per interface
- One crypto map can apply to multiple interfaces
- Tunnel source defaults to L3 outgoing interface
- Can be changed using “crypto-map local-address”
Crypto map order of operations
- Encryption applies after routing
- Static routing may be required
- Encryption applies after NAT
- NAT exemption may be required
IOS includes default fallback policies
- Default ISAKMP policies
- Can be disabled using “no crypto isakmp default policy”
- Default IPsec policies (Transform-set)
- Can be disabled using “no crypto ipsec transform-set default”

0 Comments