|
IKE_READY
*17:21:42.000: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
! Interesting packet start the process, no SAs have been created
*17:21:42.793: IPSEC(sa_request):
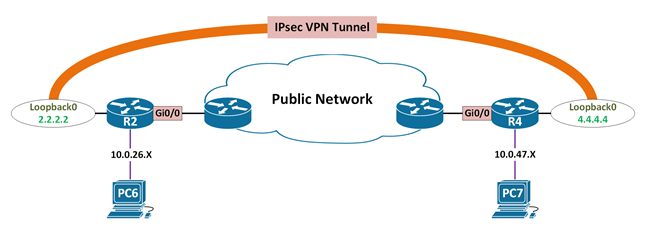
OUTBOUND local= 2.2.2.2:500, remote= 4.4.4.4:500,
local_proxy,remote_proxy,protocol,transform,(mode),lifedur
spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x0
*17:21:42.800: ISAKMP: (0):SA request profile is (NULL)
MM1 – Send Phase 1 Proposal
! Includes: Vendor IDs, Capacities, Phase 1 proposals, IKE SA
*17:21:42.801: ISAKMP: (0):Created a peer struct, New peer created, Locking peer struct, isakmp_initiator
*17:21:42.805: ISAKMP: (0):insert sa successfully sa = CAD8CC8
*17:21:42.805: ISAKMP: (0):Can not start Aggressive mode, trying Main mode.
*17:21:42.806: ISAKMP: (0):found peer pre-shared key matching 4.4.4.4
*17:21:42.808: ISAKMP: (0):constructed NAT-T * ID
*17:21:42.810: ISAKMP: (0):Old State = IKE_READY New State = IKE_I_MM1
*17:21:42.811: ISAKMP: (0):beginning Main Mode exchange
*17:21:42.812: ISAKMP-PAK: (0):sending packet (I) MM_NO_STATE
MM2 – Receive and check Phase 1 Proposal
! Includes: Chosen ISAKMP policy, IKE SA
*17:21:42.857: ISAKMP-PAK: (0):received packet (I) MM_NO_STATE
*17:21:42.858: ISAKMP: (0):Old State = IKE_I_MM1 New State = IKE_I_MM2
*17:21:42.861: ISAKMP: (0):processing SA payload.
*17:21:42.861: ISAKMP: (0):processing Unity/DPD, NAT-T, pre-shared, xauth
*17:21:42.863: ISAKMP: (0):Checking ISAKMP transform 1 against priority 10 policy
*17:21:42.864: ISAKMP: (0):encryption, hash, DH group, auth, life
*17:21:42.866: ISAKMP: (0):atts are acceptable. (…)
MM3 – Send DH public key, NONCE, NAT-D, Vendor ID
! Includes: NAT-D payload, hash, DH exchange initiation, DPD support
*17:21:42.869: ISAKMP: (0):processing vendor id payload (Unity/DPD, NAT-T)
*17:21:42.875: ISAKMP-PAK: (0):sending packet (I) MM_SA_SETUP
*17:21:42.878: ISAKMP: (0):Old State = IKE_I_MM2 New State = IKE_I_MM3
MM4 – Receive and process DH public key, NONCE, NAT-D, Vendor ID
! Includes: Determine NAT, Continuation of DH exchange, Vendor ID
*17:21:42.899: ISAKMP-PAK: (0):received packet (I) MM_SA_SETUP
*17:21:42.900: ISAKMP: (0):Old State = IKE_I_MM3 New State = IKE_I_MM4
*17:21:42.903: ISAKMP: (0):processing KE, NONCE payload, pre-shared key, vendor ID, NAT-D
*17:21:42.911: ISAKMP: (1004):No NAT Found for self or peer
MM5 – DH exchange is done, shared secret generated, send Identity
! Includes: Remote peer identity (ID)
*17:21:42.915: ISAKMP: (1004):Send initial contact
*17:21:42.916: ISAKMP: (1004):pre-shared key authentication, payload details
*17:21:42.918: ISAKMP-PAK: (1004):sending packet (I) MM_KEY_EXCH
*17:21:42.921: ISAKMP: (1004):Old State = IKE_I_MM4 New State = IKE_I_MM5
MM6 – Receive peer Identity, authenticating peer, Phase 1 is established
! Includes: rekey times started, remote identity, decision to land on a profile
*17:21:42.950: ISAKMP-PAK: (1004):received packet (I) MM_KEY_EXCH
*17:21:42.951: ISAKMP: (0):processing payload (authenticating HASH)
*17:21:42.954: ISAKMP: (1004):SA authentication status: authenticated (with 4.4.4.4)
*17:21:42.956: ISAKMP: (1004):Old State = IKE_I_MM5 New State = IKE_I_MM6
*17:21:42.964: ISAKMP: (1004):Old State = IKE_I_MM6 New State = IKE_P1_COMPLETE
QM1 – Start Phase 2, send Phase 2 Proposal
! Includes: remote and local proxy IDs, transform set(s)
*17:21:42.966: ISAKMP: (1004):beginning Quick Mode exchange, M-ID, QM Initiator gets spi
*17:21:42.969: ISAKMP-PAK: (1004):sending packet (I) QM_IDLE
*17:21:42.972: ISAKMP: (1004):Old State = IKE_QM_READY New State = IKE_QM_I_QM1
QM2 – Receive and check Phase 2 Proposal
! Includes: confirmation of Proxy ID, tunnel type, PFS
*17:21:43.031: ISAKMP-PAK: (1004):received packet (I) QM_IDLE
*17:21:43.032: ISAKMP: (1004):processing HASH, SA payload.
*17:21:43.033: ISAKMP: (1004):Checking IPSec proposal 1, transform 1
*17:21:43.033: ISAKMP: (1004):protocol, encr, mode, lifedur, hash, PFS
*17:21:43.037: ISAKMP: (1004):atts are acceptable.
*17:21:43.038: IPSEC(validate_proposal_request): local/remote_proxy, protocol, transform, lifedur, spi
*17:21:43.040: Crypto mapdb : proxy_match
*17:21:43.040: (ipsec_process_proposal)Map Accepted: MAP1, 10
*17:21:43.041: ISAKMP: (1004):processing NONCE, KE, ID payload
*17:21:43.052: ISAKMP: (1004):Old State = IKE_QM_I_QM1 New State = IKE_QM_IPSEC_INSTALL_AWAIT
QM3 – Create IPsec SA, send Phase 2 completion, Phase 2 complete
! Includes: SPI to pass traffic
*17:21:43.055: IPSEC(key_engine): got a queue event with 1 KMI message(s)
*17:21:43.062: IPSEC(create_sa): sa created, outbound sa, inbound sa
*17:21:43.073: ISAKMP: (1004):Successfully installed IPSEC SA (SPI:outbound) on GigabitEthernet0/0
*17:21:43.078: ISAKMP-PAK: (1004):sending packet (I) QM_IDLE
*17:21:43.080: ISAKMP: (1004):deleting node, reason “No Error”, IPSEC_INSTALL_DONE
|

0 Comments