IPsec VPN Dynamic Crypto Map RRI Example
|
Applied version
|
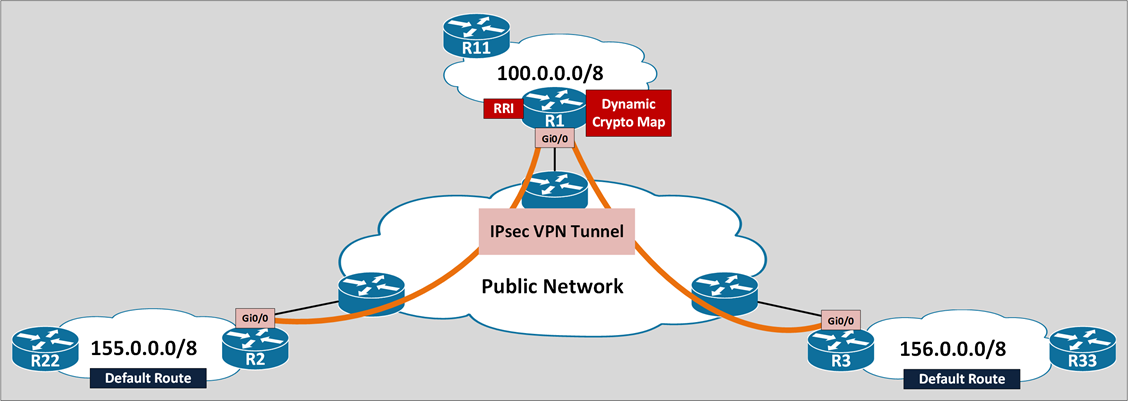
Crypto session need to be established first
- R22/R33 need to initiate traffic to R11 first
- R11 can’t initiate the crypto session
After crypto session established
- Supported traffic pattern: Hub and spoke
- R22 to R11 (or) R11 to R22
- R33 to R11 (or) R11 to R33
- Unsuported traffic pattern: Spoke to spoke
- R22 to R33 (or) R33 to R22
Configuration & Verification
| !! R1 !! | !! R2 !! |
|
! Routing #show ip route [BGP to R2] 50.0.24.0/24 [20/0] via 50.0.14.4, Gi0/0 [BGP to R3] 50.0.34.0/24 [20/0] via 50.0.14.4, Gi0/0
[OSPF neighbor to R11] #redistribute static subnets
! Crypto endpoint authentication crypto isakmp key ISAKMP_SECRET address 0.0.0.0
! ISAKMP/IKE Phase 1 security parameters crypto isakmp policy 10 encryption des hash md5 authentication pre-share group 2
! ISAKMP/IKE Phase 2 security parameters crypto ipsec transform-set IPSEC_XFORM esp-des esp-md5-hmac mode tunnel
! Crypto map parameters crypto dynamic-map DMAP1 10 set transform-set IPSEC_XFORM set pfs group2 reverse-route crypto map MAP1 10 ipsec-isakmp dynamic DMAP1
! Crypto map source address crypto map MAP1 local-address Gi0/0
! Apply crypto map interface GigabitEthernet0/0 crypto map MAP1
|
! Routing #show ip route [Static to ISP] 0.0.0.0/0 [1/0] via 50.0.24.4, Gi0/0 [BGP to R1] 50.0.14.0/24 [20/0] via 50.0.24.4, Gi0/0
[OSPF neighbor to R22] #default-information originate
! Crypto endpoint authentication crypto isakmp key ISAKMP_SECRET address 50.0.14.1
! Proxy ACL ip access-list extended ADDR150 permit ip 155.0.0.0 0.255.255.255 100.0.0.0 0.255.255.255
! ISAKMP/IKE Phase 1 security parameters crypto isakmp policy 10 encryption des hash md5 authentication pre-share group 2
! ISAKMP/IKE Phase 2 security parameters crypto ipsec transform-set IPSEC_XFORM esp-des esp-md5-hmac mode tunnel
! Crypto map parameters crypto map MAP1 10 ipsec-isakmp set peer 50.0.14.1 set transform-set IPSEC_XFORM set pfs group2 match address ADDR150
! Crypto map source address crypto map MAP1 local-address Gi0/0
! Apply crypto map interface GigabitEthernet0/0 crypto map MAP1
|
|
! Reset security association R1#clear crypto session
! Crypto session R1#show crypto session Interface: GigabitEthernet0/0 Session status: UP-ACTIVE Peer: 50.0.24.2 port 500 Session ID: 0 IKEv1 SA: local 50.0.14.1/500 remote 50.0.24.2/500 Active IPSEC FLOW: permit ip 100.0.0.0/255.0.0.0 155.0.0.0/255.0.0.0 Active SAs: 2, origin: dynamic crypto map
R1#show ip route [Static from RRI] 155.0.0.0/8 [1/0] via 50.0.24.2 R11#show ip route [O E2 from RRI] 155.0.0.0/8 [110/20] via 100.0.1.1, Eth0/0 |
! Initiate crypto session R22#ping 100.0.1.11 .!!!! Success rate is 80 percent (4/5)
! Crypto session R2#show crypto session Interface: GigabitEthernet0/0 Session status: UP-ACTIVE Peer: 50.0.14.1 port 500 Session ID: 0 IKEv1 SA: local 50.0.24.2/500 remote 50.0.14.1/500 Active IPSEC FLOW: permit ip 155.0.0.0/255.0.0.0 100.0.0.0/255.0.0.0 Active SAs: 2, origin: crypto map
|

0 Comments