IPsec VPN Using Crypto Profile
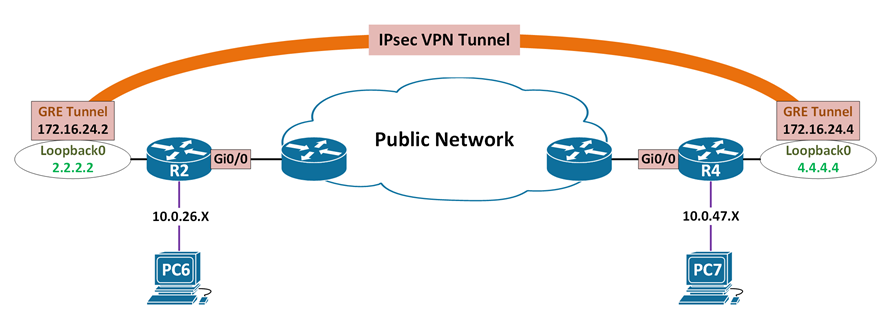
The Overview
The “Crypto Profile” configuration
- A new configuration framework of Cisco’s IPsec VPN
- The line protocol state on interface tunnel depends on IPsec SA completeness
- No longer depends on the existence of route to tunnel destination
- Replace crypto map configuration with crypto ipsec profile
- Remove the needs to specify proxy ACL, peer address
- Crypto profile is applied on interface tunnel (not physical interface)
GRE over IPsec “Transport Mode” with Crypto Profile difference
| !! R2 !! | !! R4 !! |
|
! Proxy ACL (deleted) ip access-list extended GRE2_TO_4 permit gre host 2.2.2.2 host 4.4.4.4
! Crypto map parameters (deleted) crypto map MAP1 local-address Loopback0
crypto map MAP1 10 ipsec-isakmp set peer 4.4.4.4 set transform-set XF set pfs group2 match address GRE2_TO_4
! Crypto profile parameters crypto ipsec profile IPSEC_PROFILE set transform-set XF set pfs group2
! Apply crypto map (deleted) interface GigabitEthernet0/0 crypto map MAP1
! Apply crypto profile interface Tunnel24 tunnel protection ipsec profile IPSEC_PROFILE |
! Proxy ACL (deleted) ip access-list extended GRE4_TO_2 permit gre host 4.4.4.4 host 2.2.2.2
! Crypto map parameters (deleted) crypto map MAP1 local-address Loopback0
crypto map MAP1 10 ipsec-isakmp set peer 2.2.2.2 set transform-set XF set pfs group2 match address GRE4_TO_2
! Crypto profile parameters crypto ipsec profile IPSEC_PROFILE set transform-set XF set pfs group2
! Apply crypto map (deleted) interface GigabitEthernet0/0 crypto map MAP1
! Apply crypto profile interface Tunnel24 tunnel protection ipsec profile IPSEC_PROFILE |

0 Comments