BIG-IP DNS Clustering With iQuery
Overall Network Topology (Figure 1)
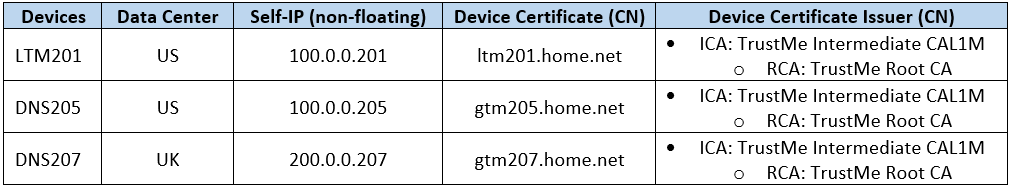
F5 BIG-IP DNS Clustering Overview
BIG-IP DNS also uses iQuery to make a cluster, via GSLB sync group with synchronization.
- BIG-IP DNS205 (gtmd process) connect to anoother BIG-IP DNS207 (big3d agent)
- BIG-IP DNS207 (gtmd process) connect to anoother BIG-IP DNS205 (big3d agent)
- iQuery runs on top of SSL/TLS connection via TCP port 4353
- To form the cluster, you need to use “gtm_add” script, run over SSH and iQuery
iQuery Integration: DNS205 With DNS207 (Figure2)
iQuery High-Level Requirements
- DNS205 (gtmd) establish iQuery connection to itself (big3d – SSL/TCP-4353)
- DNS205 (gtmd) establish iQuery connection to LTM201 (big3d – SSL/TCP-4353)
- DNS205 (gtmd) establish iQuery connection to DNS207 (big3d – SSL/TCP-4353)
- DNS207 (gtmd) establish iQuery connection to itself (big3d – SSL/TCP-4353)
- DNS207 (gtmd) establish iQuery connection to LTM201 (big3d – SSL/TCP-4353)
- DNS207 (gtmd) establish iQuery connection to DNS205 (big3d – SSL/TCP-4353)
- Established iQuery SSL trust between iQuery devices (LTM201, DNS205, and DNS207)
GTM205 Overall Configuration
- DNS ›› Settings : GSLB : General
- modify gtm global-settings general synchronization-group-name GTM_HOME_NET
- modify gtm global-settings general synchronization yes
- DNS ›› GSLB : Data Centers : Data Center List
- create gtm datacenter DC_UK location “United Kingdom”
- DNS ›› GSLB : Servers : Server List
- create gtm server DNS207 datacenter DC_UK devices add { DNS207 { addresses add { 200.0.0.207 } } }
- System ›› Certificate Management : Device Certificate Management : Device Certificate
- CN: gtm201.home.net (Issuer: TrustMe Intermediate CA L1M)
- TrustMe Intermediate CA L1M (Issuer: TrustMe Root CA)
- TrustMe Root CA (Issuer: Self)
GTM207 Overall Configuration
- System ›› Certificate Management : Device Certificate Management : Device Certificate
- CN: gtm207.home.net (Issuer: TrustMe Intermediate CA L1M)
- TrustMe Intermediate CA L1M (Issuer: TrustMe Root CA)
- TrustMe Root CA (Issuer: Self)
The Use of “gtm_add” script is mandatory (Figure 7)
Preparation before running the script:
- LTM201 (Figure 3) (optional, can be done later)
- GTM205 (Figure 4)
- GTM207 (Figure 5) (no GSLB configuration)
*For the required certificates imported, there are many combination, please refer to “Authenticated iQuery configuration” (Figure 14,15)
Use “gtm_add” script to make GTM devices become 1 cluster. (Figure 6)
- Run the script from GTM207 (empty), remote GTM target is GTM205
- First stage (Figure 7)
- Establish SSH trust (Import GTM205 SSH RSA fingerprint)
- Rekeying Master Key (Copy from GTM207)
- Shutdown services
- gtmd, zrd, named
- SSL certificates exchange (Figure 8,9)
- You can also do manual exchange (import/export)
- iQuery communication
- Verify iQuery connection
- Retrieve remote GTM/GSLB configuration
- Retrieve remote DNS/named configuration
- iQuery syncher
- Initialize iqyncher (iqsh)
- Restarting services
- gtmd, zrd, named
*If successful, all GSLB configuration will be synced between GTM205 and GTM207.
GMT iQuery Caveats
If for some reason GTM207 (gtmd) can’t establish iQuery connection to LTM201 (big3d). (Figure 10)
- GTM207 will ask GTM205 to relay the GTM207 device certificate to LTM201
- But the CA certificates (if any), won’t get relayed
- This might not be useful for the case of CA-signed device certificate
The SSL certificate exchange (between GTM207 and LTM201) can be done via bigip_add also.
- Normally you only need to run the script from one of the BIG-IP DNS sync group members.
- The remaining sync group members then attempt to connect to the big3d agent on the BIG-IP LTM system and copy their certificates to the BIG-IP LTM system.
- If BIG-IP DNS (other sync group member) can’t connect to BIG-IP LTM (big3d)
- The BIG-IP DNS in which you ran the script will relay the certificate of that particular BIG-IP DNS
iQuery Connection and Authentication
iQuery SSL handshake messages (Figure 11)
- BIG-IP DNS205 (gtmd) ––SSL over TCP-4353–> BIG-IP DNS205 (big3d) <– Internal connection
- BIG-IP DNS205 (gtmd) ––SSL over TCP-4353–> BIG-IP LTM201 (big3d)
- BIG-IP DNS205 (gtmd) ––SSL over TCP-4353–> BIG-IP DNS207 (big3d)
- BIG-IP DNS207 (gtmd) ––SSL over TCP-4353–> BIG-IP DNS207 (big3d) <– Internal connection
- BIG-IP DNS207 (gtmd) ––SSL over TCP-4353–> BIG-IP LTM201 (big3d)
- BIG-IP DNS207 (gtmd) ––SSL over TCP-4353–> BIG-IP DNS205 (big3d)
iQuery connections (Figure 12)
- View from Linux connection table
- View from TMOS connection table
iQuery authentication (Figure 13)
- DNS207 send its device certificate
- Certificate(s)
- DNS207 device certificate
- Its local CA certificate(s), if exist in “Device Trust Certificates” store
- DNS205 authenticate DNS207 certificate(s), check against its “Trusted Server Certificates” store
- Certificate(s)
- DNS205 send its device certificate
- Certificate
- DNS207 authenticate DNS205 certificate, check against its “Device Trust Certificates” store
(and vice-versa)
- DNS205 send its device certificate
- Certificate(s)
- DNS205 device certificate
- Its local CA certificate(s), if exist in “Device Trust Certificates” store
- DNS207 authenticate DNS205 certificate(s), check against its “Trusted Server Certificates” store
- Certificate(s)
- DNS207 send its device certificate
- Certificate
- DNS205 authenticate DNS207 certificate, check against its “Device Trust Certificates” store
Authenticated iQuery configuration
- Mandatory (Minimum Configuration): good for troubleshooting knowledge (Figure 14)
- Optional (Maximum Configuration): good for deployment practice (Figure 15)

0 Comments