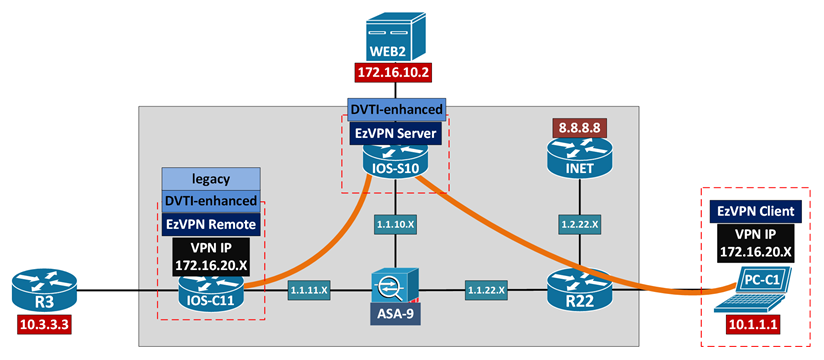
IPsec VPN With DVTI-EEzVPN Routing
|
Applied version
|
EzVPN Server interface Tunnel properties
- Encapsulation TUNNEL
- Tunnel vaccess, cloned from Virtual-Template2
- Tunnel source 1.1.10.10, destination 1.1.22.22
- Tunnel protocol/transport IPSEC/IP
- Tunnel protection via IPSec (profile “IPSEC_PROF_G1“)
IOS-S10#show ip interface virtual-access1
- Interface is unnumbered. Using address of Loopback10 (10.10.10.10)
- Inbound access list is DENY_PING_ONLY
- Post encapsulation features: IPSEC Post-encap output classification
Configuration & Verification
| !! EzVPN Server !! | !! EzVPN Client + EzVPN Remote !! |
|
! Routing via auto-RRI S 172.16.20.105/32 is directly connected, Virtual-Access1 S 172.16.20.106/32 [1/0], Virtual-Access2 S 172.16.20.107/32 [1/0], Virtual-Access2
! IPsec VPN session IOS-S10 #show crypto session detail
//to Cisco VPN Client Interface: Virtual-Access1 Username: user1 Profile: ISAKMP_PROF_G2 Group: EZVPN_GROUP2 Assigned address: 172.16.20.105 Uptime: 00:01:35 Session status: UP-ACTIVE Peer: 1.1.22.22 port 63141 fvrf: (none) ivrf: (none) Phase1_id: EZVPN_GROUP2 Desc: (none) Session ID: 0 IKEv1 SA: local 1.1.10.10/4500 remote 1.1.22.22/63141 Active Capabilities:CXN connid:1006 lifetime:23:58:23 IPSEC FLOW: permit ip 0.0.0.0/0.0.0.0 host 172.16.20.105 Active SAs: 2, origin: crypto map Inbound: #pkts dec’ed 11 drop 0 life (KB/Sec) 4362967/3504 Outbound: #pkts enc’ed 11 drop 0 life (KB/Sec) 4362967/3504
//to legacy EzVPN Remote Interface: Virtual-Access2 Username: user1 Profile: ISAKMP_PROF_G1 Group: EZVPN_GROUP1 Assigned address: 172.16.20.106 Uptime: 00:01:04 Session status: UP-ACTIVE Peer: 1.1.11.11 port 500 fvrf: (none) ivrf: (none) Phase1_id: EZVPN_GROUP1 Desc: (none) Session ID: 0 IKEv1 SA: local 1.1.10.10/500 remote 1.1.11.11/500 Active Capabilities:CX connid:1007 lifetime:23:58:55 IPSEC FLOW: permit ip 0.0.0.0/0.0.0.0 host 172.16.20.106 Active SAs: 2, origin: crypto map Inbound: #pkts dec’ed 5 drop 0 life (KB/Sec) 4179192/3535 Outbound: #pkts enc’ed 5 drop 0 life (KB/Sec) 4179192/3535
//to enhanced EzVPN Remote Interface: Virtual-Access2 Username: user1 Profile: ISAKMP_PROF_G1 Group: EZVPN_GROUP1 Assigned address: 172.16.20.107 Uptime: 00:04:30 Session status: UP-ACTIVE Peer: 1.1.11.11 port 500 fvrf: (none) ivrf: (none) Phase1_id: EZVPN_GROUP1 Desc: (none) Session ID: 0 IKEv1 SA: local 1.1.10.10/500 remote 1.1.11.11/500 Active Capabilities:CX connid:1008 lifetime:23:55:29 IPSEC FLOW: permit ip 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0 Active SAs: 2, origin: crypto map Inbound: #pkts dec’ed 5 drop 0 life (KB/Sec) 4179192/3329 Outbound: #pkts enc’ed 5 drop 0 life (KB/Sec) 4179192/3329 |
!! Cisco VPN Client ! Outgoing routing (PC-C1-to-WEB2) s=172.16.20.105, d=172.16.10.2
//Go to IPsec VPN encapsulation process s=10.1.1.1, d=1.1.10.10
!! Enhanced EzVPN Remote Routing via auto-RRI (split tunneling) S 172.16.10.0/24 [1/0], Virtual-Access1 //Don’t use manual static route IOS-C11(config)#no ip route 172.16.10.0 255.255.255.0 Ethernet0/0 1.1.11.9
! Outgoing routing (R3-to-WEB2) IOS-C11# s=10.3.3.3 (Ethernet0/1), d=172.16.10.2, MCI Check s=172.16.20.108 (Ethernet0/1), d=172.16.10.2 (Virtual-Access1)
s=1.1.11.11 (local), d=1.1.10.10 (Ethernet0/0)
! Incoming routing (WEB2-to-R3) IOS-C11# s=1.1.10.10 (Ethernet0/0), d=1.1.11.11
s=1.1.10.10 (Ethernet0/0), d=1.1.11.11 (Ethernet0/0)
s=172.16.10.2 (Virtual-Access1), d=10.3.3.3
s=172.16.10.2 (Virtual-Access1), d=10.3.3.3 (Ethernet0/1)
|

0 Comments